
By 2026, the world will be buzzing with over 80 billion connected devices. From wearables to industrial sensors, technological innovation continues to drive smarter living. But these devices also expand the attack surface for cyber threats. Weak authentication, unpatched software, and inconsistent security standards can expose networks to risk.
To mitigate these risks, organizations must strengthen their defenses with comprehensive IoT cybersecurity frameworks that integrate network segmentation, real-time threat monitoring, and AI-driven anomaly detection, ensuring that innovation and security coexist. In this blog, we explore how IoT security rests on three pillars, confidentiality, integrity, and availability, which make connected systems resilient and trustworthy.
Strengthen your IoT foundation with Niveus
IoT data security is built on three key pillars: confidentiality, integrity, and availability (CIA). Together, they form the backbone of a secure, connected world. Confidentiality keeps sensitive data out of the wrong hands. Integrity ensures that information remains accurate and untampered with. Availability guarantees uninterrupted access even under attack. These three pillars make an IoT ecosystem not just smart but also safe, trustworthy, and resilient, essential elements of any IoT data security best practices strategy.
Data Confidentiality – Protecting Information in Transit
In the IoT ecosystem, devices constantly share sensitive data, from sensor readings and system logs to user info, without proper protection, making it extremely vulnerable in transit. Shockingly, studies show that up to 98% of IoT device traffic is unencrypted. That means nearly all of that data could be intercepted or exposed.
Even more alarming, over 57% of IoT devices were found to be susceptible to traffic interception or manipulation. To maintain trust, preserve privacy, and safeguard system integrity, enforcing data confidentiality is non-optional; it’s mission-critical.
- Encrypting MQTT Communication with TLS: The MQTT protocol, used in IoT for lightweight messaging, is vulnerable to interception without encryption. To secure communications, TLS encrypts MQTT traffic between devices and brokers, preventing unauthorized access and ensuring data confidentiality during transit.
- Implementing End-to-End Encryption (E2EE): End-to-End Encryption (E2EE) enhances security by encrypting data at the source, ensuring only the intended recipient can decrypt it. This prevents access to messages by intermediate brokers or network nodes. When combined with TLS, organizations ensure complete confidentiality, securing data throughout its journey from edge devices to cloud platforms, a core element of IoT data security best practices.
Data Integrity – Ensuring the Accuracy and Authenticity of Data
In IoT networks where millions of data packets move every second, even a small alteration can have major consequences, from false sensor readings to system failures. Data integrity ensures that the information received is exactly what was sent, accurate, unaltered, and authentic. It’s what keeps IoT systems reliable and decisions trustworthy.
In fact, recent studies suggest that over 60% of IoT security incidents involve data manipulation or corruption, highlighting the need for integrity checks within any effective IoT cybersecurity framework.
Using Digital Signatures and Message Authentication Codes (MAC):
To protect integrity, IoT systems employ two key cryptographic techniques, Digital Signatures and Message Authentication Codes (MAC).
- Digital Signatures use asymmetric encryption, through which the sender signs the data with a private key and the recipient verifies it using a public key. This confirms the authenticity of the sender and guarantees that the data hasn’t been altered.
- MACs, on the other hand, rely on symmetric encryption, through which both sender and receiver share a secret key to generate and verify a unique code based on the message content.
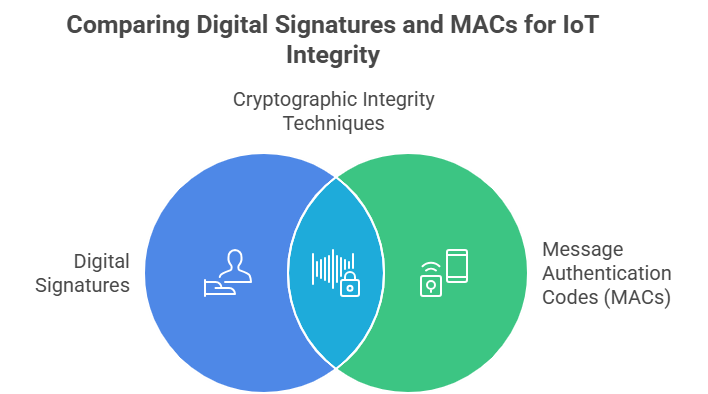
Figure 1: Visual Illustration of Comparing Digital Signatures and MACs for IoT Integrity
Data Availability – Keeping IoT Systems Reliable and Resilient
In IoT communication, reliable message delivery is crucial to maintain system consistency and performance. The Message Queuing Telemetry Transport (MQTT) protocol addresses this through its Quality of Service (QoS) levels, allowing developers to balance reliability with bandwidth and latency requirements.
- QoS 0 – At most once: Messages are delivered without acknowledgment. It’s the fastest option but offers minimal reliability, ideal for non-critical data such as sensor readings sent frequently.
- QoS 1 – At least once: Ensures that each message reaches its destination, but duplicates may occur if acknowledgments are lost. This level is suited for moderately critical updates where data redundancy is acceptable.
- QoS 2 – Exactly once: Guarantees that each message is delivered only once, preventing duplication. Although it involves higher overhead, it’s essential for mission-critical IoT operations such as financial transactions or control commands.
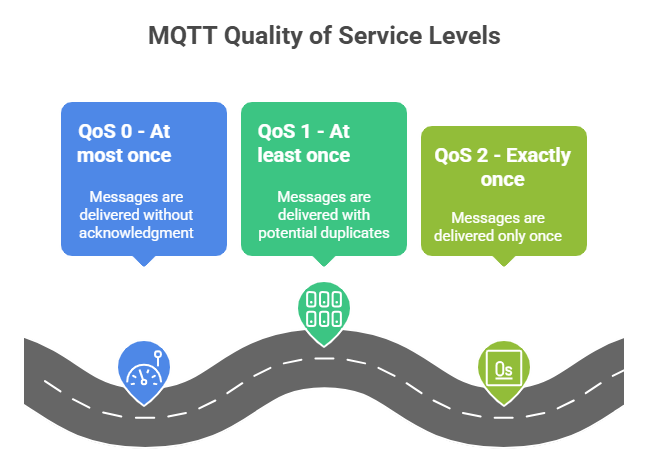
Figure 2: Visual Illustration of MQTT Quality of Service level
Selecting the right QoS level allows organizations to optimize network efficiency and message reliability as per the specific needs of their IoT applications.
Protecting Against DoS Attacks
IoT brokers, which manage communication between connected devices, are prime targets for Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks aimed at overwhelming system resources and disrupting operations. To safeguard against such threats, organizations must implement a multi-layered defense strategy that combines proactive monitoring and access management.
Key Mitigation Measures:
- Traffic Filtering: Detect and block malicious or suspicious traffic patterns before they ever reach the broker.
- Rate-Limiting: Regulate the number of requests each client can send, preventing bandwidth hogging and resource exhaustion.
- Intrusion Detection Systems (IDS): Continuously monitor network activity to identify and respond to abnormal patterns in real time.
- Access Controls and Authentication: Restrict broker access strictly to trusted devices and verified users, reducing exposure to external threats.
Together, these defenses ensure continuous system availability and maintain stable IoT operations, even under potential attack conditions.
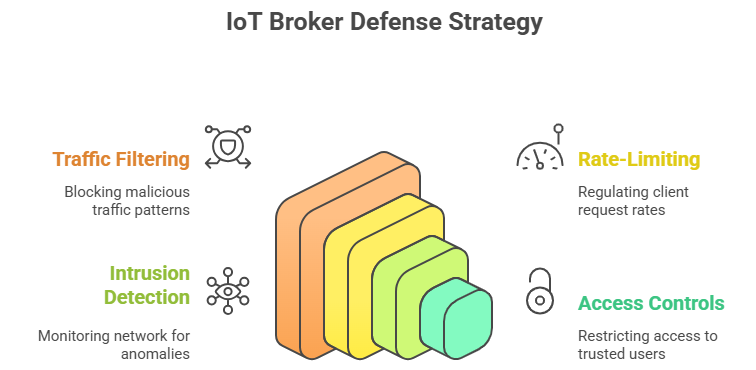
Figure 3: Visual Illustration of IoT Broker Defense Strategy
Summary – Building a Secure IoT Ingestion Framework
As the IoT landscape rapidly expands, security can no longer be an afterthought; it’s the backbone of trust in a connected world. Safeguarding every data exchange through confidentiality, integrity, and availability ensures that connected systems don’t just operate efficiently, but securely. By combining encryption, authentication, and proactive threat defense, organizations can build resilient IoT ecosystems that can withstand evolving cyber threats, empowering innovation without compromising safety.
A robust IoT cybersecurity framework aligned with IoT data security best practices empowers innovation without compromising safety, turning connected systems into trusted, intelligent networks of the future.
Read our whitepaper on Security in IoT Data Ingestion to explore how encryption, authentication, and secure communication protocols can strengthen IoT ecosystems against modern cyber threats.











