

Did you know that the worldwide cost of cybercrime is expected to reach $11.9 trillion in 2026, and a staggering $19.7 trillion by 2030? As digital ecosystems continue to leverage cloud, IoT, and AI-powered devices, hackers are also advancing in exploiting new entry points. This blog examines the modern cyber threat landscape, focusing on contemporary attacks on data pipelines, the significance of securing IoT ingestion, and the application of frameworks such as the CIA Triad and Zero Trust.
Safeguard your enterprise with AI-powered protection
The surge in financial data underscores the importance of securing the data pipeline-the most vulnerable aspect of today’s digital ecosystem. Since IoT significantly extends the network perimeter, protecting data flow from the edge to the cloud should be your top priority. Since IoT significantly extends the network perimeter, protecting data flow from the edge to the cloud should be your top priority.
The Key Types of Modern Cyber Threats
a. Ransomware & Malware Attacks
Ransomware and malware attacks are malicious software that infiltrate systems, encrypting, stealing, or destroying critical data, often halting business operations. They exploit vulnerabilities, demand ransom, and usually involve threats of data leaks. This can lead to significant financial losses, prolonged downtime, data breaches, and regulatory penalties, often crippling business operations for weeks or months, resulting in permanent data loss and regulatory fines.
According to reports, in the first quarter of 2025, approximately 2,314 ransomware victims were mentioned on leak sites, representing a 213% increase from Q1 2024.
- Example: LockBit ransomware has targeted global enterprises, encrypting files and demanding payment for decryption keys while threatening to leak stolen information.
b. Phishing & Social Engineering
Phishing and social engineering are other major components of the modern cyber threat landscape. These deceptive attacks manipulate individuals into revealing sensitive information or performing risky actions by exploiting human trust rather than technical vulnerabilities. Attackers often use legitimate-looking emails, messages, or even deepfakes to deceive victims.
Phishing and Social Engineering attacks can lead to severe consequences such as financial fraud, data breaches, and unauthorized access, causing long-term reputational damage, regulatory penalties, and customer trust erosion.
In the quarter Feb–Apr 2025, there were ~661,783 phishing attacks reported and ~553,345 unique domains used for phishing.
c. Insider Threats
Insider threats involve misuse of authorized access by employees, contractors, or partners to compromise an organization’s data, systems, or operations, often due to malicious intent, negligence, or lack of awareness. Intellectual property theft, data leaks, and compliance violations (e.g., GDPR, HIPAA), often difficult to detect and can erode trust internally and externally.
- Example: An employee with privileged access exfiltrates intellectual property or misconfigures critical systems, intentionally or unintentionally.
d. Cloud Misconfigurations & API Exploits
Cloud misconfigurations and API exploits are common vulnerabilities in modern infrastructures, resulting from human error, poor governance, or a lack of visibility in complex cloud environments. These vulnerabilities allow attackers to access or manipulate sensitive data.
Data exposures, unauthorized access to sensitive data or systems, compliance breaches, and extended time to detection. For instance, misconfigured cloud storage can expose large volumes of customer data, triggering fines and remediation costs.
- Example: A storage bucket left open publicly (no authentication) or an API endpoint without rate-limiting or proper access controls.
e. Supply Chain & Third-Party Attacks
Supply Chain and Third-Party Attacks exploit vulnerabilities in an organization’s ecosystem, compromising trusted systems or injecting malicious code into software updates, enabling them to infiltrate multiple organizations simultaneously, making it difficult to trace and contain.
Widespread infection across multiple organizations, loss of trust with partners, large-scale remediation costs, and extended business disruption.
- Example: A software provider’s build pipeline is compromised, enabling attackers to embed malicious code that is distributed to thousands of customers.
f. AI-Driven & Adversarial Attacks
AI-driven and adversarial attacks use AI to automate, scale, and enhance cyberattacks, including phishing content and deepfakes. In adversarial attacks, threat actors manipulate machine learning models, leading to incorrect decisions and undermining AI-driven security systems.
Faster, harder-to-detect breaches; misinformation campaigns; corrupted analytics or AI models; erosion of trust in automated systems. 79% of detections in one report were malware-free, signaling more stealthy, AI-enabled attacks.
- Example: Deepfake voice calls that impersonate a CEO ordering a finance transfer, or poisoned training data that causes an ML-based detection system to fail.
g. IoT & Edge Device Vulnerabilities
IoT and edge device vulnerabilities occur when devices like sensors, cameras, and industrial controllers lack proper security controls, allowing attackers to gain unauthorized network access, intercept data, and disrupt operations.
Network infiltration, hijacking of data flows, disruption of industrial/operational systems, potential physical-world consequences (especially in OT/ICS environments).
- Example: A smart CCTV camera with default credentials gives attackers a pivot into the corporate network, or a sensor in a manufacturing line is exploited to disrupt operations.
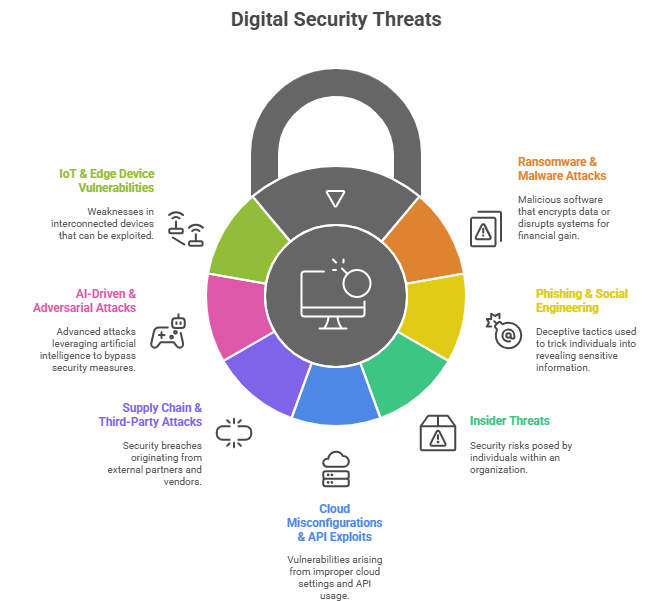
Figure 1: Visual illustration of the Key Types of Modern Cyber Threats
The Ripple Effect: How These Threats Impact Businesses
Cyber threats today extend far beyond IT departments; their effects ripple across every facet of a business, from finances and operations to brand equity and long-term strategy.
- Financial Loss: Data breaches can result in ransom payments, forensic investigations, and system restoration, with hidden costs like legal fees, customer compensation, and increased insurance premiums. In 2025, the average total cost was $4.88 million, with large-scale ransomware incidents exceeding $10 million.
- Operational Disruption: Ransomware attacks can cause significant disruptions to mission-critical systems, leading to average downtime exceeding 20 days. Supply chain breaches can cause delays, productivity loss, and broken SLAs in industries like manufacturing, BFSI, and healthcare.
- Reputational Harm: Data breaches can lead to a reputational fallout, with over 60% of consumers losing trust and nearly half shifting to competitors. Rebuilding trust requires transparency, investment, and time, all at a cost.
- Regulatory Consequences: GDPR, HIPAA, and PCI DSS regulations tighten enforcement, causing non-compliance to attract fines and legal scrutiny, with GDPR violations potentially affecting 4% of global annual turnover..
- Strategic Delays: Security breaches can hinder innovation and growth, as IT teams prioritize containment and compliance over digital transformation, AI, and cloud migrations, causing a security debt.
In simple terms, cyber risks no longer result in isolated technological problems. They disrupt the very foundations of business resiliency and strategy. The real cost is not just what is taken, but also what is delayed, lost, or never built as a result of them.
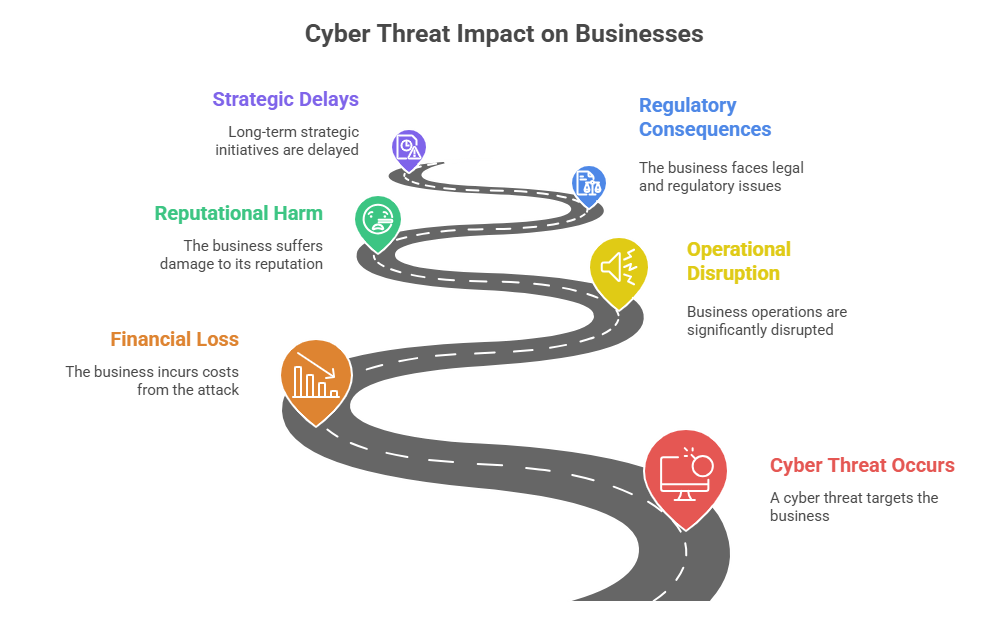
Figure 2: Visual Illustration of cyber threat impact on business
Building Resilience: Defensive Strategies
As cyber threats evolve in scale and sophistication, building organizational resilience requires a proactive, multi-dimensional defense strategy.
- Zero Trust Adoption: Transition from perimeter-based security to Zero Trust architecture, ensuring continuous verification of users, devices, and connections to minimize insider risks and prevent lateral movement.
- Multi-Layered Security Posture: Layered defenses, including strong encryption, IAM, endpoint protection, and continuous monitoring, are essential for reducing single points of failure in data, identity, network, and cloud environments.
- Security Automation & AI-Based Detection: AI-driven analytics and automated incident response can detect anomalies, prioritize alerts, and contain threats in real-time, enhancing response speed and reducing manual intervention in modern attacks.
- Employee Awareness & Cybersecurity Culture: Regular security training and phishing simulations are crucial for preventing human error and fostering a culture where employees recognize and report suspicious behavior.
Together, these strategies shift cybersecurity from a reactive posture to a resilient, adaptive framework, enabling businesses to anticipate, withstand, and recover from threats faster than ever.
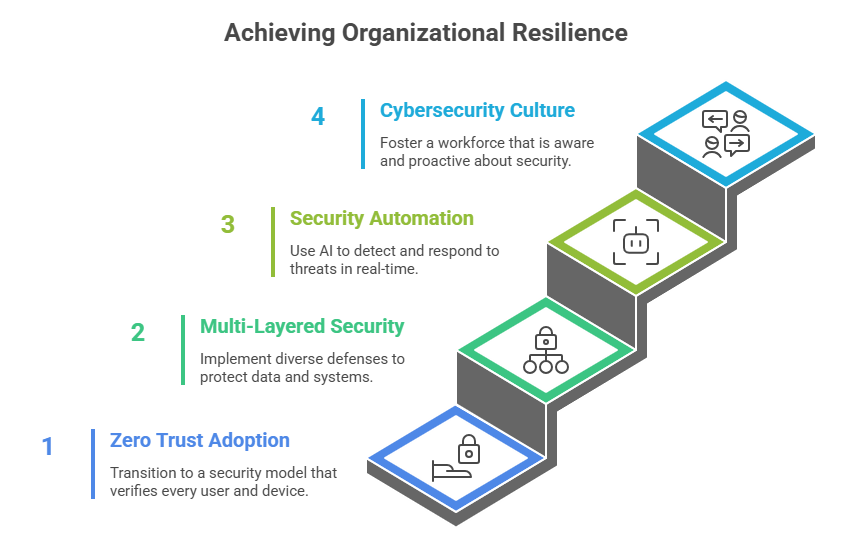
Figure 3: Visual illustration of building Resilience: Defensive Strategies
Niveus Partnership
Partnering with cloud security experts like Niveus and Google Cloud empowers organizations to build a secure, compliant, and future-ready digital foundation. Through deep expertise in Google Cloud’s Security Stack, Niveus helps enterprises design and implement end-to-end protection strategies across infrastructure, data, and identity.
By integrating Zero Trust principles, AI-powered threat detection, and compliance automation, Niveus enables businesses to proactively identify vulnerabilities, mitigate risks, and maintain visibility across hybrid and multi-cloud environments.
With a strong focus on resilience, scalability, and regulatory alignment, the Niveus–Google Cloud partnership ensures that security isn’t just a safeguard but a strategic advantage, empowering organizations to innovate confidently in an increasingly hostile cyber landscape.
Conclusion: A Call for Continuous Vigilance
In today’s hyperconnected world, cybersecurity is not a one-time implementation; it’s an ongoing discipline that evolves with every new technology and threat. The rapid rise of ransomware, AI-driven attacks, and cloud vulnerabilities underscores the need for continuous monitoring, modernization, and readiness.
Organizations that invest proactively in modern architectures, Zero Trust frameworks, and threat intelligence can stay ahead of attackers, rather than just reacting to them. The path to true cyber resilience lies in staying vigilant and treating security as a living, adaptive practice that evolves alongside the business itself.
Read our whitepaper on Security in IoT Data Ingestion to explore how encryption, authentication, and secure communication protocols can strengthen IoT ecosystems against modern cyber threats.











