
The growth of IoT devices generates around 2.5 quintillion bytes of data every day, posing substantial security issues for data input. These systems are vulnerable to unauthorised access, data spoofing, and denial-of-service assaults, jeopardising their reliability and integrity. A proposed solution is to strengthen the data input pipeline, with a focus on robust encryption and authentication. This blog will discuss critical security measures for protecting IoT infrastructure, including mutual TLS and enhanced monitoring.
Protect every device, every connection, discover how with Niveus
The journey of IoT data from device to cloud is fraught with risks. Unauthorized access to MQTT brokers or data streams allows attackers to steal sensitive information or inject false data. Devices can be spoofed or compromised, tricking the pipeline into accepting malicious inputs. Furthermore, data in transit is vulnerable to interception if encryption is not implemented. The entire system can also be crippled by Denial-of-Service (DoS) attacks that flood the broker, rendering the system unreliable or inoperable.
Understanding MQTT and Its Security Challenges
MQTT (Message Queuing Telemetry Transport) is one of the most widely used lightweight messaging protocols for IoT communication. Designed for low-bandwidth and high-latency networks, it enables efficient device-to-cloud and device-to-device data exchange. However, its simplicity and minimal overhead often come at the cost of robust built-in security, making MQTT-based IoT ingestion pipelines vulnerable to multiple threats.
Key Security Challenges
- Lack of encryption in the default setup: By default, MQTT transmits messages in plain text. Without SSL/TLS encryption, data can be intercepted or altered during transmission, exposing sensitive device information and telemetry data to attackers.
- Weak authentication and authorization: Many MQTT deployments often rely on anonymous or default credentials, which pose a security risk by allowing unauthorized access. The absence of strong authentication and role-based authorization enables malicious actors to access sensitive topics.
- Susceptibility to message tampering and data spoofing: Attackers can disrupt systems by injecting false data or altering legitimate messages when integrity checks are absent, potentially resulting in erroneous analytics or triggering unintended actions in automated systems.
- Broker compromise or misconfiguration: The MQTT broker is crucial for communication; misconfiguration, such as granting unrestricted topic access or using outdated software, can expose it to denial-of-service attacks, unauthorized data extraction, or system compromise.
In short, while MQTT remains an efficient protocol for IoT data ingestion, it demands strong security controls and best practices to safeguard device communications and maintain data integrity.
Methods to Enhance IoT Data Security
As IoT ecosystems expand, securing the data pipeline, from devices to the cloud, becomes critical. Strengthening MQTT communication requires a multi-layered approach involving secure configurations, authentication mechanisms, and proactive monitoring systems. Below are key methods to enhance IoT data security.
1. Secure MQTT Broker Configuration
The MQTT broker acts as the central message hub, responsible for routing all communication between devices and applications. Securing this component is essential to prevent data leakage, unauthorized access, and service disruption.
How to secure your broker:
- Implement strong authentication, authorization, and encryption to ensure only trusted entities can connect.
- Use strong credentials or tokens for device authentication to prevent unauthorized logins.
- Enforce least-privilege access through topic-level authorization, ensuring devices access only what they need.
- Enable TLS encryption to protect data in transit from interception or tampering.
- Disable unused protocols and ports to reduce the attack surface and block unwanted connections.
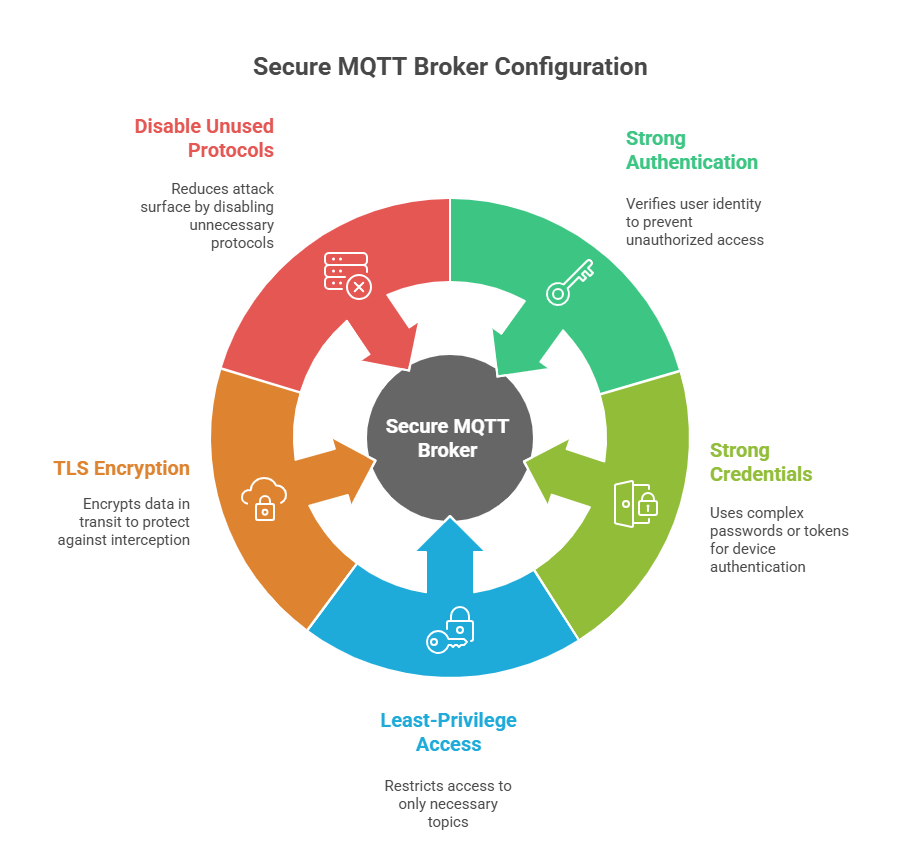
Figure 1: Visual Illustration of MOTT Publish-Subscribe Encryption Model
2. Mutual Authentication
Mutual authentication (or two-way SSL/TLS) ensures that both the client and broker verify each other’s identities before any data exchange occurs.
- Devices present client certificates, and brokers respond with server certificates, both of which are validated by trusted Certificate Authorities (CAs).
- This two-way verification prevents man-in-the-middle (MITM) attacks, where attackers impersonate legitimate devices or brokers.
- Implementation tip: Use short-lived certificates with automated renewal to enable efficient key rotation and minimize the impact of compromised credentials.
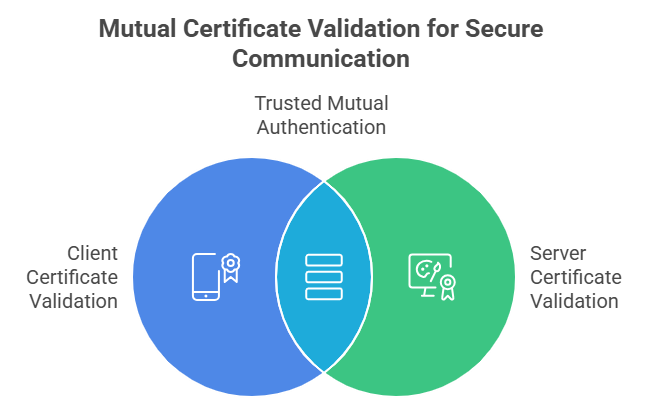
Figure 2: Visual Illustration of mutual certificate validation for secure communication
3. Access Control Lists (ACLs)
Access Control Lists provide fine-grained control over who can publish or subscribe to specific MQTT topics, reducing the risk of unauthorized message flow.
How ACLs work:
- Use client identifiers, usernames, and topics to define permissions.
- Apply read-only or read-write access depending on device role.
- Set group-level restrictions so only authorized devices in specific roles or locations can communicate.
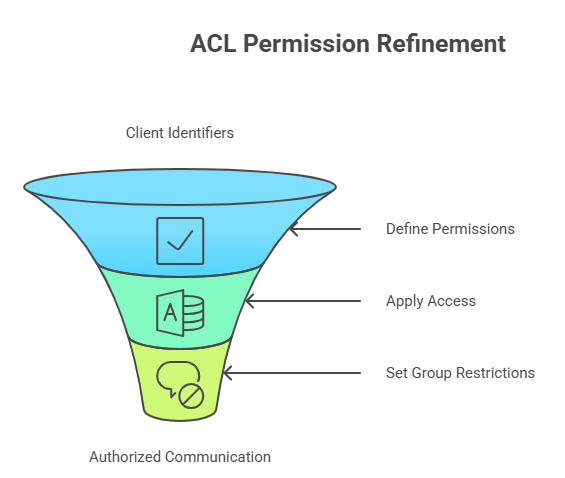
Figure 3: Visual Illustration of ACL Permission Refinement
4. Secure Communication
Ensuring end-to-end encryption of MQTT traffic safeguards sensitive telemetry data from eavesdropping or manipulation.
Best practices:
- Encrypt MQTT sessions using TLS/SSL.
- Enforce strong cipher suites and modern key exchange algorithms to prevent cryptographic weaknesses.
- Implement forward secrecy to ensure past communications remain secure even if a key is later compromised.
Figure 4: Visual Illustration of MQTT Security Measures
Use a security checklist for compliance:
- Minimum TLS 1.2 or higher
- Certificate validation on both ends
- Certificate pinning for IoT devices to verify only trusted servers.
.
5. Intrusion Detection and Prevention Systems (IDPS)
To proactively monitor and protect MQTT networks, organizations can deploy Intrusion Detection and Prevention Systems (IDPS). These systems analyze network traffic to detect and respond to anomalies in real time.
How IDPS enhances MQTT security:
- Continuously inspects MQTT traffic to identify suspicious activities and compares them with known attack patterns.
- Provides real-time alerts and can automatically block malicious IPs or payloads.
- Integrates with Security Information and Event Management (SIEM) tools for continuous monitoring and incident response.
Benefits:
- Early detection of threats before they cause a major impact
- Reduced downtime through automated responses
- Centralized visibility and analytics across IoT environments
Figure 5: Visual Illustration of IDPS Architecture
Advanced IoT Security Enhancements
While securing MQTT communication is vital, true IoT resilience requires protection across every layer, from endpoints to networks and governance. The following advanced measures help organizations strengthen their overall IoT security posture.
1. Endpoint and Device-Level Security
IoT devices form the foundation of the ecosystem, making them a prime target for attackers. Securing devices from the firmware up is critical to maintaining system integrity.
Key practices:
- Secure boot and firmware signing: Ensure devices boot only trusted firmware by verifying digital signatures at startup. This prevents unauthorized code from running on edge devices.
- Device identity lifecycle management: Assign unique cryptographic identities to each device and manage them, from onboarding to decommissioning.
- Remote attestation: Continuously verify device integrity by confirming that firmware and configurations remain unaltered since deployment.
Together, these practices establish device trust and prevent rogue or compromised endpoints from entering the network.
2. Data Integrity and Validation
Data authenticity and consistency are crucial in IoT systems where decisions rely on continuous telemetry streams.
Best practices:
- Use hashing or digital signatures to verify that messages haven’t been modified in transit or storage.
- Implement blockchain-based or Merkle-tree mechanisms for tamper-proof data logging and verifiable audit trails.
These cryptographic measures ensure that every data point, from sensors to analytics, is validated and trustworthy.
3. Network-Level Protection
Protecting the IoT network layer ensures that even if a device is compromised, lateral movement and data exposure are minimized.
Recommended strategies:
- Use VPNs, private networks, or Zero Trust Network Access (ZTNA) models to limit device communication to trusted entities.
- Apply network segmentation by isolating MQTT brokers and IoT gateways from the general internet, reducing the risk of external exploitation.
These controls add a layer of defense, containing threats and ensuring that sensitive components remain protected.
4. Monitoring, Auditing, and Logging
Ongoing visibility into IoT environments is essential for early threat detection and compliance readiness.
Implementation approaches:
- Enable continuous monitoring using Security Information and Event Management (SIEM) systems or cloud-native tools such as Google Chronicle and Cloud Logging.
- Maintain detailed audit trails for device communications, broker access, firmware updates, and configuration changes.
These logs provide forensic evidence during incidents and support proactive anomaly detection.
5. Compliance and Security Governance
Strong governance frameworks ensure that IoT systems align with international best practices and regulatory requirements.
Recommended standards:
- ISO/IEC 27001: Information Security Management
- NIST IoT Cybersecurity Framework: Risk-based IoT security guidance
- OWASP IoT Top 10: Common IoT vulnerabilities and mitigations
Organizations should enforce policy-driven data governance, conduct regular security assessments, and perform periodic penetration testing to validate system resilience and compliance.
Implementing IoT Security – Niveus Approach
At Niveus, we help organizations build secure, scalable, and intelligent IoT ecosystems on Google Cloud. Our implementations are designed to safeguard every layer of the IoT data pipeline, from device connectivity to data storage and analytics, while ensuring performance and compliance.
Leveraging Google Cloud Capabilities
- Cloud IoT Core (legacy) / Pub/Sub for secure ingestion: MQTT device data is securely transmitted to Google Cloud via Pub/Sub, enabling encrypted, authenticated streaming and reliable communication between edge devices and cloud services during legacy IoT Core migrations.
- Cloud Armor and VPC Service Controls for network-level protection: These services utilize IP-based access policies, filter traffic, and protect sensitive IoT resources through a zero-trust approach, reducing the attack surface and mitigating DDoS attacks or unauthorized access.
- Chronicle Security Operations for threat detection and response: Using Google Chronicle, Niveus enables real-time analytics to correlate IoT events with enterprise telemetry, identifying anomalies before they escalate.
- Cloud Key Management Service (KMS) for encryption key handling: Cloud KMS provides centralized control of encryption keys, automated key rotation, and granular access policies, ensuring compliance with data protection standards.
Conclusion: Building Trust in IoT Data
In today’s hyper-connected landscape, trust is the true backbone of IoT. Building it means going beyond one-time fixes. It’s about creating a living security ecosystem powered by strong authentication, encryption, and continuous monitoring.
As devices and threats evolve, so must defenses. By adopting layered security strategies and leveraging cloud-native tools such as Google Cloud, organizations can ensure that every interaction remains authentic, private, and resilient. In IoT, trust is not configured once; it is continually earned.
Read our whitepaper on Security in IoT Data Ingestion to explore how encryption, authentication, and secure communication protocols can strengthen IoT ecosystems against modern cyber threats.











