

As you break down your monolithic approach into microservices, you’ll have plenty of benefits such as scalability, better up-time, and better monitoring. But there’s a hitch of using microservices- the risk of attack is greater. Moreover, all the communication within the microservices is exposed to the network. Thus, securing your microservices should be a key consideration on your transformation journey.

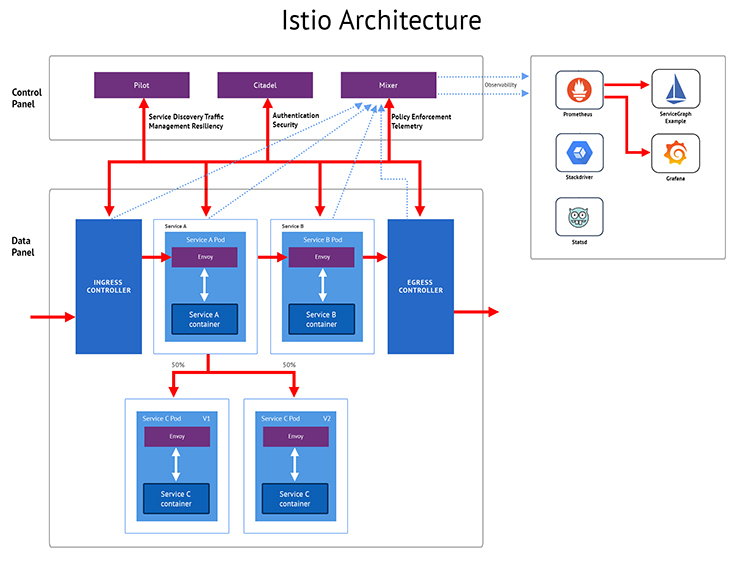
Istio manages the collection of microservices, thereby authenticating one service to another, and handles the loads. It also brings a failover feature that can help in the recovery from any issues that may cause the app to malfunction. It also specifies the flow of data through the network. It lets you connect, monitor, and secure microservices deployed on-premise, in the cloud, or with orchestration platforms like Kubernetes.
One of the major advantages of Istio is that it offers exclusive service mesh security and policy administration to microservices. But a significant thing to note is that although a service mesh puts in numerous vital security features, it is not the entirety regarding the microservices security. To ensure that you’re completely safe against today’s threats, it’s also essential to think through an approach around the network security, which can identify and nullify attacks on the service mesh infrastructure.
Istio helps you to make sure that only the services that are supposed to communicate with each other are doing that. It lets you encrypt those communications to provide protection against attacks that can take place when those particular services interact and let you apply application-wide policy.
Here are the advantages that Istio offers:
• Security at the Edge
Configuring individual security policies and protocols in Kubernetes needs administrative investment. Istio can consolidate these activities while adding a layer of security that lets you monitor and focus on negotiating traffic as it comes into the mesh.
Istio combines with Kubernetes as an ingress controller and maintains the load balancing for ingress. This helps you to enhance and add a level of security at the edge with ingress rules. This allows you to apply to monitor around whatever is entering the mesh and utilize route rules to administer compromising traffic at the edge.
The Role-Based Access Control (RBAC) in Istio makes sure that only authorized users are allowed in the mesh, thereby providing customizable and flexible control of access at the service-level, namespace-level, and method-level.
• Monitoring
In Istio, the structure of the full metrics pipeline is a part of its design. Envoy sidecars functioning at the Pod level connect metrics to Mixer that manages policies and telemetry. Furthermore, Prometheus and Grafana services are enabled by default. These metrics and visualization tools let you access current information about services and workloads in a single place.
The Istio Dashboard comprises of three key sections that help in monitoring:Individual Workloads View: This section offers metrics about requests and responses for every individual workload within the mesh. This will also show the metrics about inbound workloads and outbound services for these workloads.
Individual Services View: This offers you the metrics about requests and responses for every individual service within the mesh. Also, it provides metrics about client and service workloads for this service.
A Summary View of the Mesh: This offers an overall summary view of the Mesh and shows HTTP/gRPC and TCP workloads within the Service Mesh.
A service mesh, like Istio, has the capacity to change how traffic can navigate through the mesh. Also, it empowers the developer a capability to deal with traffic in their desired way.
• Operational Agility
More significantly, Istio’s service mesh provides the control required to manage traffic distribution with complete independence from deployment scaling. This helps in reducing the risk of releasing a new code with the help of Canary deployment.
The concept behind canary deployment is to release a new version of service by initially testing it using a small percentage of user traffic, and then if everything goes well, gradually increasing the percentage of user traffic while concurrently phasing out the old version. This ensures that if something goes wrong, you can easily abort and rollback to the older version.
How Niveus Has Helped Its Clients with the Istio Service Mesh
Although cloud-native architectures provide agility and speed, one of the drawbacks is complexity. When monolithic apps are broken down into many microservices, it can comprise of hundreds of moving parts. If not properly managed, it can be really difficult and cause disaster in terms of security. Niveus helps in connecting and routing these parts together with Istio that gives the control back to developers about how their app is functioning and where data is routed in the cloud.
Niveus helps its clients by delivering multi-cloud application services like monitoring, load balancing, and security for containerized applications using microservices-based architecture. We create Service Mesh that is integrated with Kubernetes for container orchestration and security and is completely integrated with Istio.
There’s no need for the Developers to be worried anymore about adding instrumentation to different codebases manually or about automating the infrastructure. Istio empowers them to deploy new microservices with out of the box monitoring capabilities and a single source of metrics.
Our clients can significantly de-risk their work with the level of control and visibility that Istio offers. We’ve been able to accelerate the delivery that previously would have taken much time and effort, allowing our clients to focus on our market differentiators.
We orchestra the Blue/green deployment using Istio and bring down the cycle time for release to a few hours. This has helped our customers to achieve a significant improvement in terms of productivity and speed to deliver new features and bug fixes.By summarizing on how Kubernetes manages authentication, authorization, and encryption, Istio is able to unite and encompass some of the endorsed best practices for running a secure Kubernetes cluster.
So, whether you’re already a bonafide cloud-native, or just thinking to migrate in order to modernize your IT environment, Istio can take you the rest of the way by offering you the power to manage an environment and keep it safe from all threats at the same time.











